Many professional organizations see a lot of potential in having their communication services hosted in the cloud, but have some concerns about data security. Should they be afraid of the cloud?
Do cloud services bring more benefits than they raise security concerns?
Security is a critical requirement for any organization whose key operations rely on communications. Consider an example: a push-to-talk/group communication service used on a production line to ensure smooth operation as well as safeguard personnel. Could this group communication be provided as a cloud service?
According to the Airbus survey into the professional apps market, organizations are open to the potential of services provided by the cloud. However, concerns remain about the security of cloud-based services.
Research says* 93% of organizations are moderately or extremely concerned about cloud security.
Despite these doubts, a cloud based push-to-talk service offers three specific benefits which can outweigh the related security concerns:
1 You can choose where to dedicate your resources.
2 You can get the service up and running quickly.
3 You can pick a scalable option.

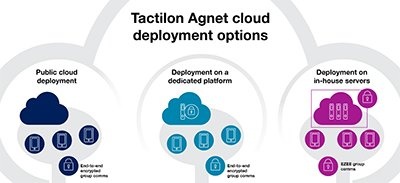
When deciding on your push-to-talk communication solution, you need to consider how you could deploy push-to-talk as a cloud service. There are three options here:
1 Public cloud deployment. Public cloud is a platform shared by several organizations (multi-tenant cloud).
2 Deployment on a dedicated platform. Dedicated platform means that you can use any data center, just like using a public cloud – the difference is the platform is reserved for your organization’s exclusive use.
3 Deployment on in-house servers and your own software licenses.
Each option has its strong points and drawbacks. Download an infographic that explains the pros and cons of each option.
Benefits from push-to-talk as a service
You can choose where to dedicate your resources
Here’s the thing: your company’s core business probably doesn’t involve maintaining your own data center. You should also dedicate your available resources to maintaining that core business, so hiring a large team of IT experts and buying servers may not be your smartest move.
And even if you wanted to hire an IT expert or two, could you be sure they would make your system as secure as you need? Not many companies can make the same security efforts as those offered by cloud service providers.
Security is a complicated and challenging concept, no matter where your data servers are.
You can get the service up and running quickly
You could choose a private, isolated set-up for your cloud service. This will take some planning as you will need to invest in data centers, and it will also take time.
In contrast, a set-up based on a public cloud can save you the costs and effort involved in building the system and carrying out maintenance and upgrades. (You will still have to plan the overall IT infrastructure and manage your devices and users.)
If you need full operational continuity while you move from your existing mobile communications to the new cloud-based service, you will need to carefully plan your IT architecture. Even so, your small pilot group could quickly adopt the cloud service, and their experiences would help plan the full-scale adoption.
You can pick a scalable option
A cloud based service will let you scale your operations with almost unprecedented speed. You can readily equip all your workers with the smartphone app and activate more subscriptions and provision new users when needed. This is practical, particularly during maintenance breaks, as the service can be scaled down as well as up.
You can also allow subcontractors to temporarily join your communication groups using their own devices. In a legacy VHF system, for example, this would be impossible – the subcontractors would need VHF walkie-talkies to join in the communications.
How to secure the push-to-talk cloud
Push-to-talk cloud services clearly bring benefits. But how secure are they?
Security – a shared responsibility
Security in the cloud operates on a shared responsibility model - a cloud provider guarantees the security of data centers for a cloud service provider, whereas the cloud service provider ensures overall service security for the customer.
As the cloud user, you are responsible for certain elements of security. As a rule, you will be responsible for security related to your own information and data, as well as your devices, accounts, and identities.
From your point of view, shared responsibility is a great deal – a one-stop shop. There’s no need to source the service and security elements from many different providers.
If your push-to-talk service is hosted on a cloud-based platform, the service provider is responsible for the security of the platform. The service provider is also in charge of enforcing data loss prevention (DLP) in the cloud and controlling how the data is shared through and in the cloud.
Moreover, the push-to-talk cloud service must be resilient to attacks, ensuring that the system and software is hardened, that events can be traced and that it offers a quick response to any risk.

Security or reliability?
According to Institute of Electronic and Electrical Engineers (IEEE) standards, reliability is the ability of a system or component to perform its required functions under stated conditions for a specified period of time. To put things bluntly, a reliable system can be trusted to work well.
The security of a system or application is related to threats and vulnerabilities. According to IEEE standards, security is the ability of a system to protect information and system resources with respect to confidentiality and integrity. In other words, a secure system is not open to intrusion.
Because professionals need their communications to be reliable and always available, cloud based communications need to have reliability assurances. This often means choosing a dedicated platform, directly connected to the private radio network. In addition, the operator of the mobile network needs to provide additional reliability assurances.
Who can access your data?
Even though data centers in a cloud may be outside your direct control, your service security is still paramount. Cloud service providers use several methods to control security, monitor activities across a platform, and enforce regulatory compliance. Despite this high degree of control, the data itself is always accessible only by the customer company – you – and not by the service provider.
The service provider also protects the exchange of data - normally by using a robust end-to-end security method. In the case of group communication services, this also includes communications made through client and platform interfaces to external systems. These systems, which trigger alerts to users, analyze the communication data or act as chat bots, must also incorporate security to protect the customer against accidental or malicious interventions.
Who can use the push-to-talk cloud service?
Your cloud service must have mechanisms to verify and control the legitimacy of the users that have access to the communications. This is because insufficient access management and account hijacking, together with authentication that is too weak, are the most common cause of security incidents.
In a critical service such as cloud-based group communications, a strong user authentication with proper encryption is essential.
What about the communication devices?
Device and application management starts with ensuring that the devices offer an adequate level of protection. This may be your responsibility, that of your mobile network operator, or of the company that sold you the devices.
On top of your reasonable housekeeping of devices, it’s a good idea to require verification when applications are first installed into devices, as well as when the apps are used – at least on each login.
The data and communications protection will not work if your confidential data can be extracted or intercepted at the device level.
In negotiations with your push-to-talk cloud service provider, you should include all these details and add any specific availability and security needs in the Service Level Agreement that you make with the provider.

How to choose the right push-to-talk cloud service
Not all cloud services are created equal – and your needs for a group communications service aren’t standard either. Depending on how mission or business critical your operations are, you may want to know about your provider’s special capabilities in providing higher availability, improving latency, ensuring redundancy or in disaster recovery.
Your cloud service provider must be willing to meet your compliance requirements for the personal information of your workers, partners and customers. Choosing a General Data Protection Regulation (GDPR) compliant service provider is the simplest way to meet this requirement.
Last but definitely not least, your service provider should be able to declare the security audits their system has passed. And if there are doubts, there’s always the possibility of conducting a third party security audit including a report with technical details.
Based on the vast but standard-based customization that a cloud can offer, a cloud service may end up being even more secure than an on-premise communication server. At the very least, it is definitely less effort and more cost efficient for someone whose core business is not running a cloud.
So, when choosing your push-to-talk service cloud, you need to consider the scalability you require, the level of responsibility you want to take and the control you want to have over the whole service.
Identify your optimal cloud set-up for smart, advanced push-to-talk services! Click on the image to download the infographic that explains and compares the Tactilon Agnet cloud deployment options:
This blog post was originally published in October 2020. It has since been updated to include a link to the most recent report on the 2022 Airbus survey into the professional apps market.
Sources:
* https://www.isc2.org/Resource-Center/Reports/Cloud-Security-Report
https://www.coursera.org/lecture/cyber-security-manufacturing/reliability-versus-security-GQIIG